Your account
Understand important concepts that will help you navigate your account and structure your company's access to Spreedly.
Logging in
Spreedly customers can explore their account configuration and performance on app.spreedly.com. If there are login issues, try a password reset from the sign-in page first, and contact us if there are further difficulties.
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) using a one-time passcode (OTP) on login is required as an additional layer of security for your account. After entering credentials and clicking Continue, an OTP is generated by the authenticator application on your mobile device. This code must also be entered into the login screen. Any authenticator application can work, including Authy, Google Authenticator, Auth0, or Guardian Microsoft Authenticator. The OTP requirement can be skipped for up to 30 days on the same browser.
The Spreedly app will prompt MFA enrollment the first time a new user logs in. We recommend taking note of the recovery codes in case of a lost password without access to an OTP. To learn more about MFA and troubleshoot any issues, visit our support page.
Single sign-on (SSO)
Spreedly also offers single sign-on (SSO) functionality to simplify user access and authentication through a connection to your identity provider (IdP). Our help center has additional detail on requesting and enabling SSO for an account and which IdPs can support this feature.
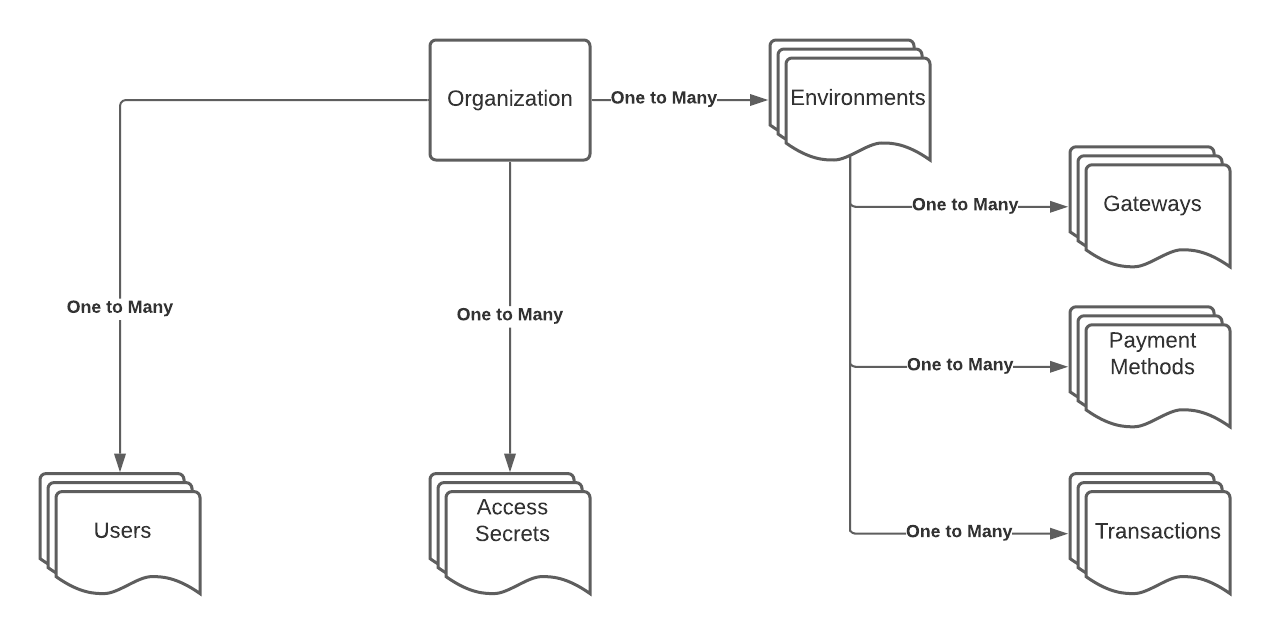
Organizations
Every user belongs to an organization. This organization is meant to represent a complete company and its connected merchant accounts. Billing occurs at the organization-level. If groups within your organization have separate billing requirements, they need to operate as independent organizations on the Spreedly application.
After logging in, any user in an organization with the Admin role can change the organization's settings from the Organization pop-out menu found at the bottom of the main navigation.
Environments
An organization can have an unlimited number of environments. Environments allow separation of payment information and payment methods into distinct groups.
Note: All environments in paid Spreedly accounts have the capability to make production transactions. There are no test-only environments.
Environments are distinct and should be used to isolate separate payment functions. For instance, a payment method stored in "Environment A" cannot be used in a purchase against a gateway that is set up in "Environment B". We recommend unique, intentional naming and categorization of environments to ensure they are purpose-built for these functions and accessible from the Spreedly app.
Calls to the Spreedly API require specification of an environment key. An environment key is not sensitive information and can be shared safely. A list of environment keys is available in the environment list page in the Spreedly application, or on the environment settings page. Navigate here by clicking the current environment name on the top-right of the application screen and selecting Environment settings or View all environments.
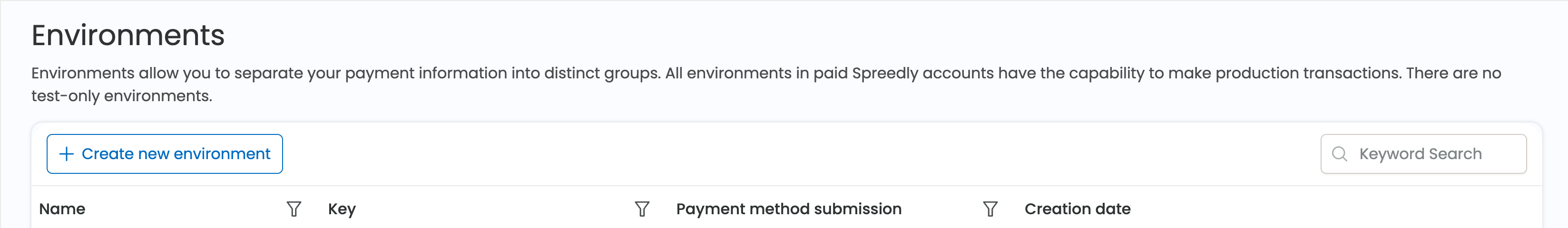
The environment list page can be searched by environment name or environment key. General environment settings for any environment can be viewed, but only the settings for your current environment can be edited. Select a new environment by clicking Switch environment on the right side of any environment in the list table, or from the top of the environment details page you want to switch to. This allows you to review transactions and manipulate configurations in the context of that environment only.
Access secrets
When using the Spreedly API, access secrets are used to authenticate to an organization. There are two types of access secrets: a single environment access secret and an organization access secret. A single environment access secret can be used to authenticate API calls for one environment, while organization access secrets can authenticate API calls for any environment. Spreedly recommends using environment access secrets in all cases, where possible, as this provides the most simple, secure method of API authentication.
To view, create, or delete environment access secrets, click the environment name on the top-left of the application screen to open the environment menu and select Access secrets. There will be a table view of access secrets created for that environment that can be partially revealed and deleted. Environment access secrets can be created from this page as well. Alternatively, environment access secrets can be managed through the Spreedly API.
Best practices:
Spreedly encourages using environment access secrets instead of organization access secrets. Environment access secrets ensure credentials will be used to authenticate API calls for the intended environment. Conversely, any organization access secret can authenticate API calls for any environment.
If organization access secrets are used, Spreedly recommends separating environments to isolate production connections and data from non-production connections and data; though there is still risk as production and non-production environments are accessible via the common organization access secret. Test/staging/QA environments should not share credentials with production environments.
Unlike environment keys, access secrets are considered private and secure. Do not share them or expose them to insecure channels, even in emails to the Spreedly team. An access secret, in combination with an environment key, grants full access to the Spreedly API. If an access secret is shared insecurely, we advise that you revoke the secret as soon as possible and generate a new one.
Spreedly recommends rotating all access secrets every 60-90 days for stronger security. To prevent any downtime, follow these steps to rotate access secrets:
- Create a new access secret and name it. Copy it down as it will not be visible after the initial creation period.
- Update applications to use the new access secret instead of the original.
- Once all applications have been updated and the new secret has been confirmed to work, login to the Spreedly application and delete the original access secret from the environment it was in, or from the organization.
User management
Only add trusted individuals from your company to the Spreedly application, and be intentional in selecting their roles. Admin users should be limited to those who are trusted to manage, access and delete the list of all users and API access secrets, or to cancel the organization's Spreedly subscription, or take other actions.
Users can be added by opening the dropdown menu found at the top right of the site header and selecting Organization users. Open the Add user experience by clicking that button on the page. Complete the form fields before selecting at least one user role and inviting the new user. Admin can remove users by clicking the dot menu to the right of their entry on theOrganization users table and selecting Remove user.
Note: Removing users prevents that user from accessing authenticated Spreedly websites like app.spreedly.com, however, API access is granted via access secrets, which could still be stored elsewhere by a removed user. We recommend that access secrets are rotated any time a user is removed as a best-practice for the security of your account.
Diagram
Updated 5 months ago
Read more about users and role-based access control (RBAC) in the Spreedly application.
